PCT Patent / Smart card applications

Method and device for qualitative saving of digitized data.
PCT Patent WO/1987/005726/p>
An encrypted signature (S) representative of the information and of the identity of the holder of those information is established by means of a calculation algorithm for the encryption and the compression of information to be saved. The signature (S) is recorded on the medium carrying the information forming the message (M). The parameters for the calculation of the signature (S), one or several secret keys, are recorded on at least one inviolable carrying medium. Application to the qualitative saving and to the protection of data, on-line or not, of data bases.
| Title | Method and device for qualitative saving of digitized data |
|---|---|
| Application Number | PCT/FR1987/000079 |
| Publication Number | 1987/005726 |
| Application Date | 18/03/1987 |
| Publication Date | 24/09/1987 |
| Inventor | Camion Paul Goutay Jean Harari Sami |
| Assignee | Infoscript Camion Paul Goutay Jean Harari Sami |
| Attorney | SCHRIMPF Robert |
| IPC | G06F 01/00 G06F 21/00 G07F 07/10 |
The present invention relates to a method and device quality of digital information stored on backup media be erased or modified. With the advent of automated processing of information, the problem of protecting access to data processed or to be treated is first installed. Although this problem, especially as regards the protection of data stored in online databases of large computer systems, could receive effective solutions, the implementation of the latter requires very utilisation.de IT resources important. However, this type of protection, recent spectacular intrusions in databases of information concerning the defense of some states data could reveal, however, can not claim to be absolute. This type of intrusion, and actually mathematically possible, shows now a problem of a different nature to the extent that these intrusions are mostly "transparent", the clever hacker can perpetrate his crime in the absence of any trace or footprint revealing his identity. The risk actually incurred because of such intrusions includes not only access to confidential or secret information, without the knowledge of the moral authority of the corresponding databases, where qualitative data integrity is respected by the intruder, but also the risk of destruction, modification in the absence or in the presence of fraudulent intent of the intruder. In particular, the trade press has been able to report a significant increase in "embezzlement without material break" by mere intrusion into the databases of financial and banking institutions and modification and fraudulent falsification of account data for these establishments.
Various works to solve a similar problem have been published recently in particular by the French Patent Application N°. 2, 514, 593.
According to the technique described in the aforementioned patent application, a message that we want to take into account the content is first subjected to a contraction, the contraction being obtained by treatment type Hamming code. A signature is then calculated on the contraction obtained by means of an encryption algorithm, the encrypted signature having a number of digits or characters to the same number of digits or characters of the contraction.
However, the technique described in the aforementioned patent application can claim to be used to perform a qualitative protection of digital data such as those contained in a database on two grounds below.
The contraction of the original message with a linear processing such as Hamming code can in no way claim to be a unique representation of the original message, different messages can generate the same contraction. Qualitative backup any texts is not possible because ultimately two different messages can produce the same contraction and therefore the same signature. Moreover, the cipher of contraction for the development of the encrypted signature is performed within the circuits of a protected memory card, the computing capacity is modest contraction and encrypted signature can at most contain only six characters.
To overcome the aforementioned drawbacks, notably in view, absolute protection of data access online databases that can not be fully guaranteed the present invention is to, to ensure a means of preserving the integrity of data scanned by qualitative protection of these recorded on a data carrier erased or modified. Another object of the present invention is to-implement a method and a device for qualitative saving of digitized data in which a signature perfectly representative of a single message or text and its author signatory is affixed the media on which the data is stored in plain text, the signature constituting a seal.
Another object of the present invention is to-implement a method and a signature device, each text, different, having a signature for a specific key, the signature being independent of the source text.
Another object of the present invention is also, in the case of information signed in accordance with the present invention by a transmission signatory holder, the possibility for the user authentication as a recipient of the integrity of information transmitted as the origin thereof.
Another object of the present invention is also the by-implement implementation of the method and device of the invention with respect to a pseudo-information between the definition of the pseudo-signer information and a receiver temporary random access code.
The process of qualitative protection of digital information stored on an erased or modified, the object of the invention support, is remarkable in that it is establishing a representative encrypted signature information and the identity of the holder this information by means of a calculation algorithm and recording it on the information carrier. The calculation parameters of the signature are stored on at least one inviolable support.
The device for the qualitative protection of digital information recorded on an erasable or modifiable support object of the invention is characterized in that it comprises first storage means in which are stored the secret keys of the or holder signed or received information and second storage means in which is stored a program for calculating one or more signatures according to the method of the invention. Means for calculating or signatures and registration of such signature or signatures on the support means to safeguard information are provided. Means for comparing the signature (S, Se) recorded on the medium of information with the calculated signature and validation means to use the information stored on the coincidence of signature (S, Se) calculated and recorded on the signature the recording information (II) are further provided carrier. Peripheral means input or data visualization enable an interactive dialogue between system and user signatory or receiving the data.
The invention is applicable as will be described in detail in the following description for the exchange of digital data between users, protection of local input files, protection against double reading data caller identification, management programs distributed network of locally programmable terminals, management of maintenance for software to manage files interned during periodic use thereof, verification of accounting transactions or management, archiving accounting or bibliographic information, conservation of library programs, backing up databases of stored locally and centrally by calculating and comparing the corresponding signatures files.
It will be better understood on reading the description and viewing the drawings below in which:
- figure 1 shows schematically the essential enablers-implement the method of the invention,
- figure 2 shows, schematically, a particularly advantageous means for setting-implement the method of the invention embodiment,
- figure 3 shows an illustrative diagram of the method of qualitative information, object of the invention, in the case where the information is transmitted to a subscribing to a backup recipient,
- figure 4 schematically shows a particularly advantageous from an algorithm for calculating the signature according to the method of the invention embodiment,
- figure 5 shows an alternative embodiment of setting-implement the algorithm, as shown in figure 4,
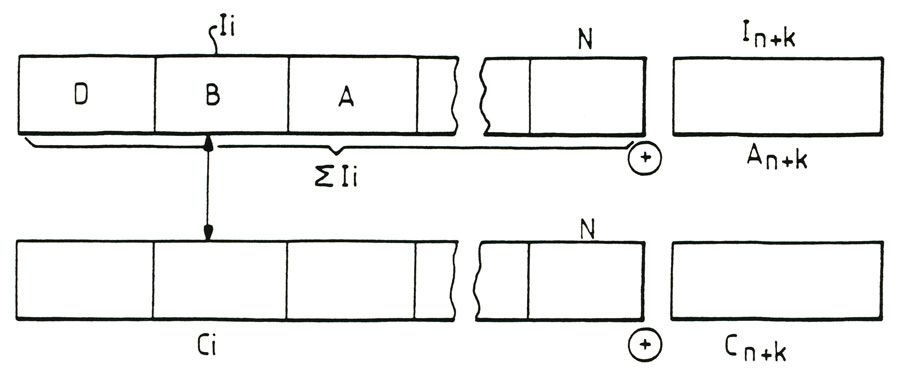
- figure 6 shows another embodiment and formatting-implement an algorithm for calculating the signature, as shown in Figure 4, in the case where a large amount of information to save the message or text component is provided,
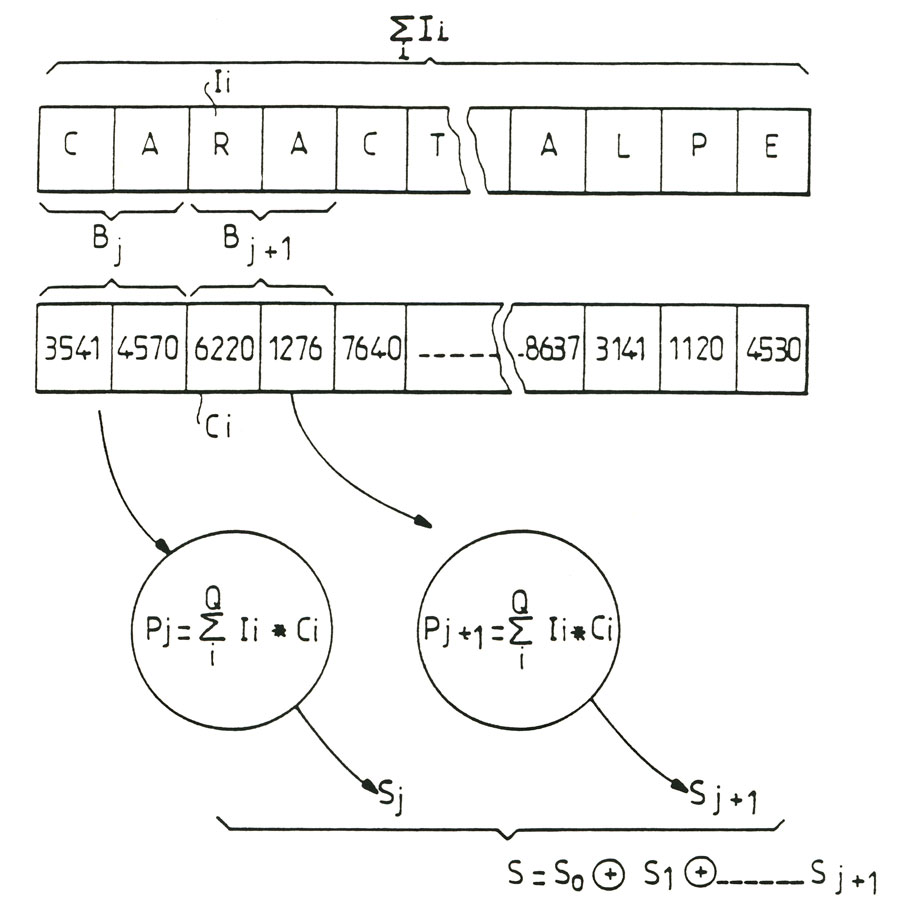
- figure 7 shows schematically a variant-implement the process of qualitative backup object of the invention, this variant is particularly advantageous for a successive hierarchy of signatures for a text message or question,
- figure 8 shows a block diagram of a device for setting-implement the method of the invention, the device is particularly suitable for carrying-implement the method of the invention,
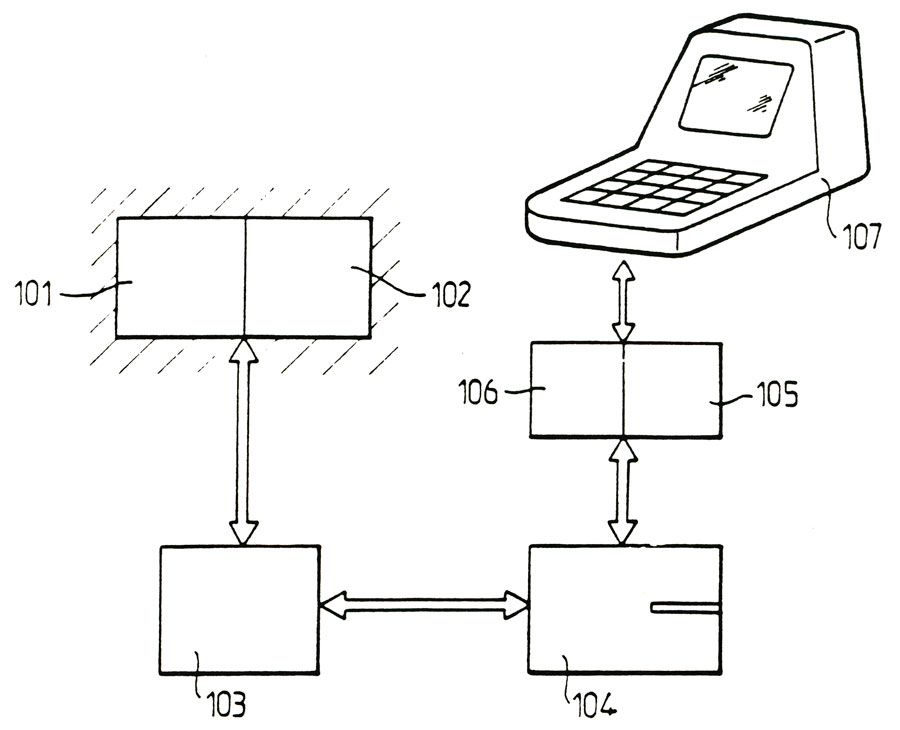
- figure 9 shows an alternative embodiment of the device for the qualitative protection of digital information recorded in the case where the amount of information of the message component is relatively reduced, and household use may be envisaged,
- figure 10 finally shows a flowchart of the functions of the device for the qualitative information scanned backup object of the invention, as shown previously in figures 8 or 9.










The method of qualitative protection of digital information recorded on an erasable medium or modified, according to the invention, will first be described in connection with figures 1 and 2.
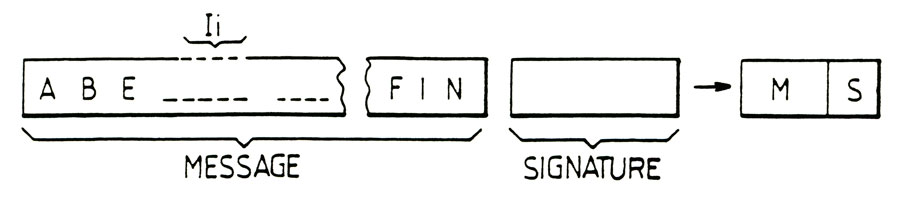
According to figure 1, the method of qualitative information backup object of the invention is to establish a representative encrypted signature, denoted S, the information and the identity of the holder of such information via a calculation algorithm. The signature S is saved on the media for information, the information constituting a text or message. The message text is stored or plain example, to safeguard the message or text or the transmission thereof. By recording clear message or text on the erased or modified support, means of course that it is recorded on this media in the absence of any encryption or any coding whatsoever to conceal meaning. The parameters for calculating the signature S is recorded on at least one holder inviolable.
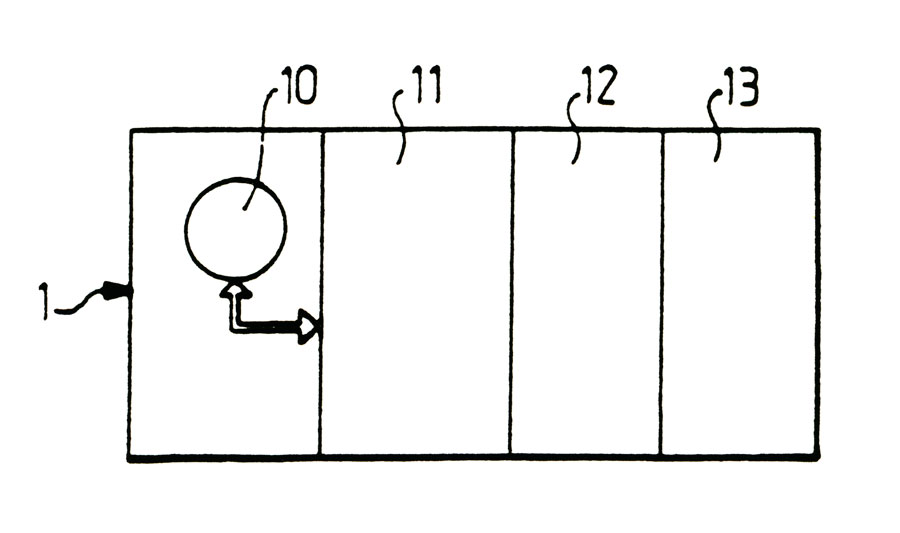
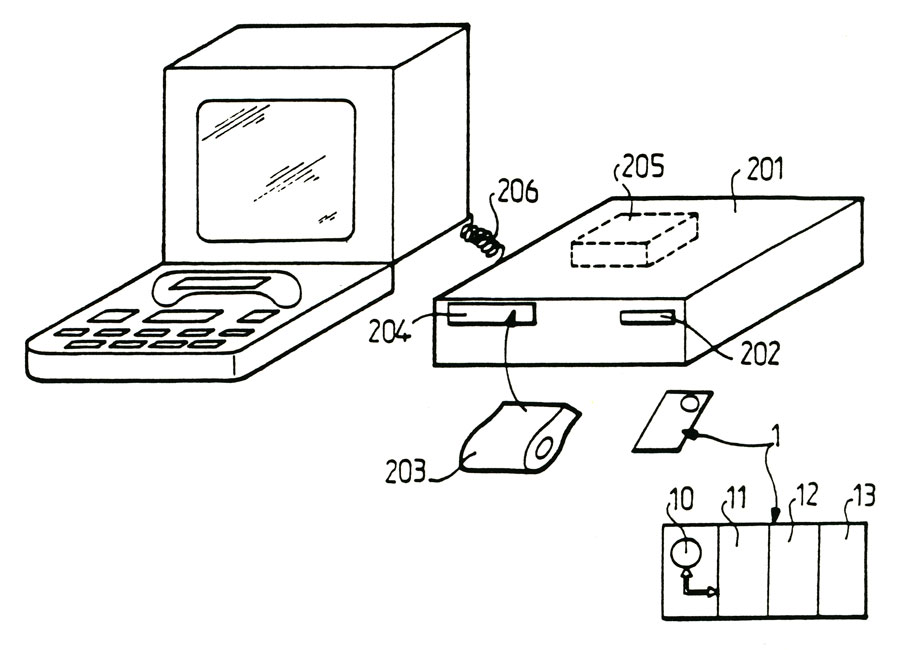
As has been shown in figure 2, the tamper resistant support can advantageously consist of a protected memory card. Figure 2 shows the protected memory card, schematically, it being deemed to have an active area 10 formed for example by a built-in map, in 11 totally unattainable secret area, protected by microprocessor the microprocessor 10, 12 in a protected and read and write accessible only after introduction of a given area code, and in a completely free area 13 for writing and reading. In Figure 2, the memory card is referenced 1 protected memory cards are normally commercially available and we can usefully refer to requests for French patent N° 74 10191 and 08184 added 75 and 75 08185 issued on 10 March 1980 for a more detailed description of devices such as memory cards protected.
In accordance with the method of the invention, the algorithm is advantageously a cipher message or text to be protected, and compression of information in the text to be protected from at least one secret key associated signatory holder information.
Of course, the encryption algorithm and compression of information noted "li" in figure 1 is selected to ensure relative independence from any particular text: S and signature generated from this text. By relative independence between the content of the text message and or calculated by means of the algorithm according to the present invention signature, it will be understood, firstly, that for a given one signature text S is obtained and on the other hand, any the slightest change in information "li" in the message or the text has the effect of generating a signature S different from the original signature in the absence of apparent correlation.
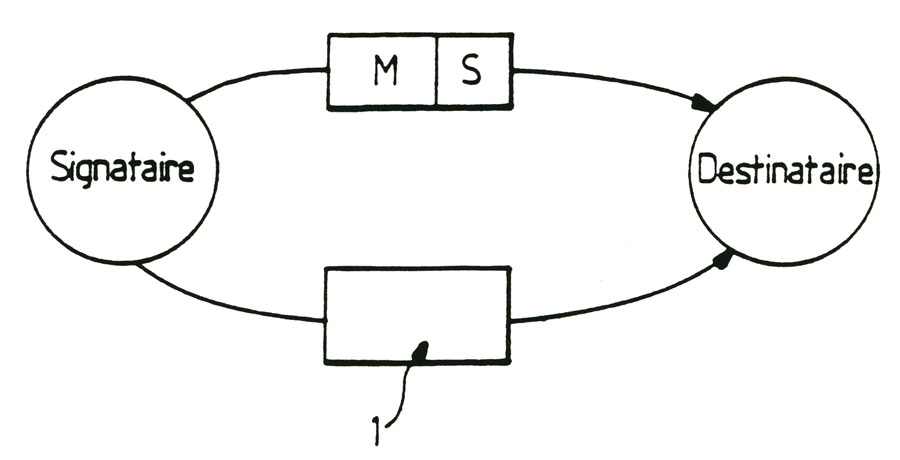
An example of particularly advantageous application of the method of qualitative scanned according to the present invention will be described backup information in association with figure 3 referring to this figure, and in particular to ensure the transmission of the saved information accordance with the method of the invention, the information to be transmitted to a recipient, the method of the invention is to address the media on which one inviolable parameters for calculating the encrypted signature S has been made to the recipient, then to send out information on the support and encrypted S recipient signature. The recipient is in possession of inviolable medium 1 which was addressed by any route, and the message M and signature S, it can to control the content of transmitted and received data from the calculation parameters the signature S contained in the support inviolable one, establish an encrypted control signarture S', from the backed up information received from the transmission. They can then compare the encrypted signature received by transmission, denoted S, and the encrypted signature control denoted S'. The identity of the saved information and information received by the destination and origin authenticated this information is then obtained in the coincidence of the encrypted signature S and S encrypted signature control.
Of course, the secret key or secret keys constituting at least part of the parameters used to calculate the signature S is recorded in the secret area unreachable protected 11 of the memory card 1 or inviolable medium, the latter having been made available to the recipient and possibly even the signatory. Storage media such as inviolable memory cards currently provide media with the tamper character is currently the best. Indeed, the mechanical structure of this type of electronic component and the integrated protection to the component by a microprocessor with memory for access thereto, ensures a high level of protection.
However, the setting-implement the method object of the invention is not limited to the use of storage medium such as inviolable memory cards protected. Indeed, it is of course consider setting-implement the process using means in which the inviolable support may consist of any actively protected circuit regarding access to data stored by a microprocessor areas or the like, and structurally by any suitable means.
A mode switch-implement the process of qualitative scanned according to the invention will now be described safeguard information in conjunction with the 4 to 7.
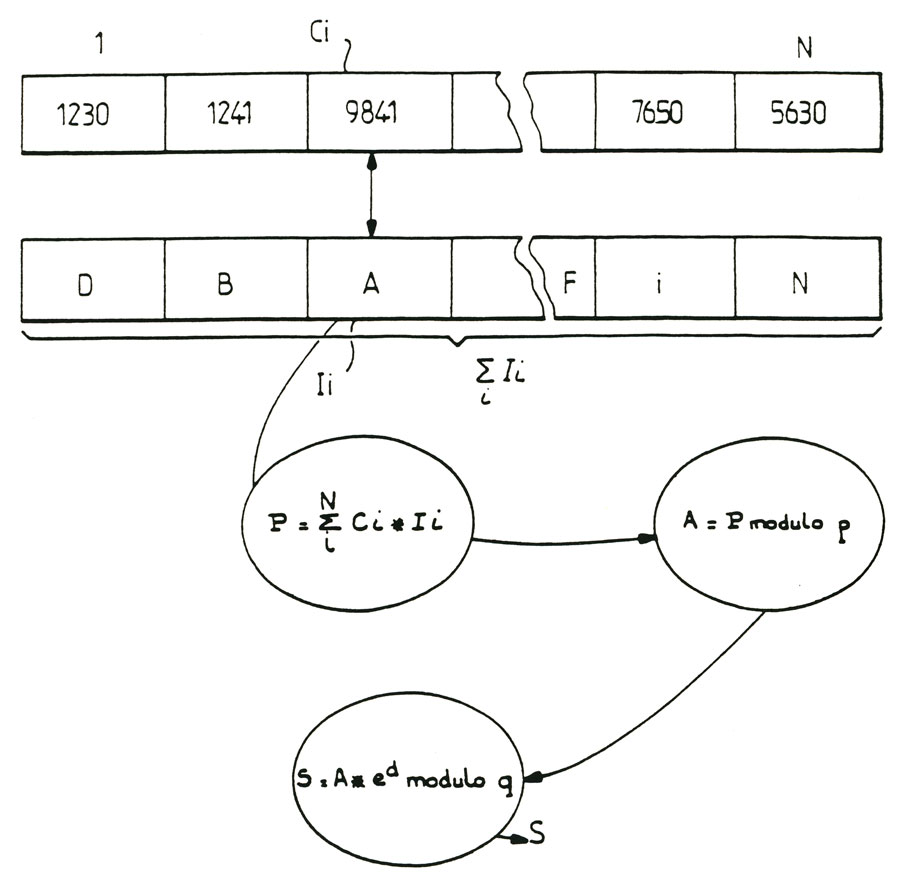
According to an advantageous feature of the method of the invention, the secret key and the signature S may consist of a word consisting of a number of characters or numerals. Signature and / or secret keys or can be of a word also including alphanumeric characters. Thus, for a word comprising "n" characters, such as alphanumeric characters such as defined by the extended ASCII code, which consists of 256 characters, the probability of obtaining the secret key or keys or optionally, for carrying-in-implement different text, the same signature S is of the order of {2S6)Tl oa at most Hθ"*n loΣSof Φ* ch-f ^3 health used. As further shown in figure 4, in order to establish the encrypted signature S Representative information and the identity of the holder of the information, the algorithm for performing encryption of data recorded "li" and the compression of this information may include, according to an advantageous embodiment, to initiate the creation a sequence of random or pseudo-random numbers only, from the secret key or keys. in Figure 4, the information "li" are rated "DBA" and so on, and random or pseudo -aléatoires several figures are rated "Ci". It thus represents a random number N in figure.
According to a particularly advantageous characteristic of the object of the invention, the sequence of random numbers denoted "Ci" includes the same number of terms "Ci" and a divisor of this number, the number of characters of li information to back up. According to the process object of the invention, the encryption algorithm allows to make the inner product, denoted by "P" / end term of the sequence of random numbers "Ci" and the save information li. The scalar product thus obtained is noted:
N p = Σ li * Ci i=1
The algorithm then allows a modular reduction of the scalar product "P" modulo p so as to define a number modulo p A = P where A is the remainder of division by p P, wherein p is an number having a first number of digits equal to the number of characters of the secret key or the signature or S. the algorithm then allows a number of modular exponentiation a so as to define a number S = a * e modulo q, where S denotes the residue of the division of A * e by q wherein q is a number having a first number of digits equal to the number of characters of the secret key or keys or signature and where d represents one or more consecutive numbers or not of the secret key or keys. The no-tare S thus obtained constitutes the encrypted signature.
To increase the cryptographic strength of the encrypted signature S, it is also possible in accordance with the method of the invention, to add to the scalar product P a random value product of random extra numbers or pseudorandom rated C + k in figure 5, and arbitrary numerical values denoted aN + k in the same figure, values such as date, time, an identification number of the information holder or a code of this identitication applicant consisting for example alphanumeric characters, or possibly a random number of a digit or more.
Of course, the characters "li" information to back up, can be added by concatenation of strings representing significant arbitrary numerical values, such as date, time, an identification number or identification code information or random as previously mentioned number holder. In this case, this additional information is directly integrated with the information recorded Σli to save. Of course, the following pseudo-random number "Ci" is then completed by random numbers designated. CN + k after supplementing.
The method of the invention as described above can be advantageously-implement in the case where the text message to save or qualitatively 250 comprises, for example alphanumeric characters. In this case, and for the most common applications, the signature S and or secret keys can then include for example, six characters or digits described.
However, the process of safeguarding quality digitized information ofcjet of the invention is not limited to this number of characters constituting the message or text. Of course, it can be advantageously used in order to save qualitatively information databases, the number of characters of this information up to several thousands. In this case, it is advantageous to use for setting-implement the method, a large capacity of computer calculation, to obtain minimum calculation time for the calculation of signatures S.
In the case described above, the information to backup "li" and the random number "Ci" may advantageously be divided into blocks marked "Bj" data, as shown in Figure 6 blocks "Bj" contain a predetermined number "Q"character and the dot product "P" is advantageously calculated for each of the blocks "Bj", so as to define partial dot products rated "Pj". Bienentendu, partial scalar products "Pj" are of the form:
Q
Pj = ∑ li * Ci i
Thus, a partial signature denoted "j" is calculated for each block "Bj" and following the "j" signature is the final signature of the representative set of information to back up. As shown in Figures also 1-6, random or pseudo-random "Ci" constituting the random number sequences are conveniently sow numbers with number 1 of numbers or characters equal to the number of characters in the or keys used. Advantageously, but not limited to, the characters "li" of information to save can be grouped so that the number of digits of each term Ci following random number exceeds the number of characters forming a group. It will be understood of course that the characters making up the information to back up, the noted character "li", are recorded in digital form, that is to say, in fact in the form of zero or 1-bit information in this case , a plurality of bits comprising the total or partial representation of a character can be grouped so as to constitute a group as defined previously. The term term product groups or characters and numbers constituting the random or pseudo-random numbers following denoted Ci is defined as the product arithmé¬ tick any group or policy nature "i" correspondent.
A particularly advantageous variant of the method of qualitative protection of digital information recorded on an erasable or modifiable medium will now be described in conjunction with figure 7.
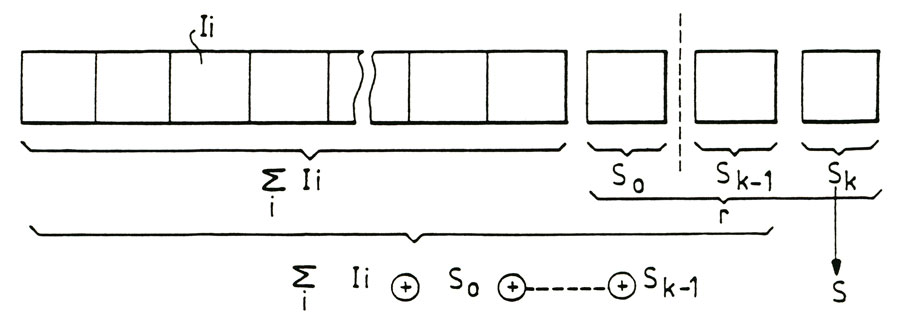
In the above figure, the method according to the invention is for the same amount of information to back up, amount of information recorded Σli corresponding to a length of text or given message, calculate iteratively a plurality denoted "r" signatures themselves denoted "Sj", successive. Of course, the signatures S_. are calculated by using the algorithm as described above by example. According to an advantageous embodiment of the method of the invention, the signatures rated Sκ_- are successively integrated as a string, information to save Σli. Signatures can be embedded for example by concatenation information Σli. Following the integration of a signature of order K-1 information Σli above, a signature of higher order Sκ is then recalculated on all the information to backup to which were added the signatures of lower order considered string. This provides a particularly interesting definition of successive signatures for a hierarchy of signatures including the final signature denoted Sκ, from signatures lower order SQ SR_1 for the same information noted Σli content. Of course, in this case the final "S" signature is in fact the "S" signature within the meaning of the method of the invention or a signature high degree of hierarchy.
Another particularly advantageous variant of the method of qualitative protection of digital information, the object of the invention may include pre alablement for inclusion on the support of li information or the inviolable support the signature S to submit further signature above to encryption processing from, for example S, a secret encryption key, so as to obtain an encrypted signature denoted Se. The encryption processing on the signature S may be made from a program encryption calculation of conventional type, such as for example a computer program known as the DES method or program. In this case, the signature is encrypted "c" and has the same number of characters than the signature S. The encryption process can of course be applied to either the signature S obtenuepar simple application of the method of invention, as already described, or due to an interactive application of the method, the signature S is then considered the last order of K obtained as already described above.
In the case where the subject to encryption processing said "S" has a number of signatures to six caractèreslimité particular 1'application described above, the encryption processing can then be performed advantageously in the inviolable medium circuits when celui- is constituted by a memory card. In this case, the encrypted signature obtained and calculated by the microprocessor of the smart card 1 is then transferred onto the support for registration information "li". Developing an encrypted signature "Se" course provides an improvement of the cryptographic strength of the signing so treated.
A more complete description of a device for implementing the method of the invention for the qualitative protection of digital information stored on an erased or modified support, will now be given with reference to figures 8-10.
As shown in Figure 8, the mechanism to ensure the quality of digital information backup object of the invention comprises first memory means rated 10T, which are stored in the secret key or keys holder signatory or recipient of information constituting li text or message to save. The second storage means 102 are also provided in which is stored a program for calculating one or more signature "S", "off", according to the method as described above in the description. Computing means noted.
103 or signatures S, Se and registration.
104 signatures of those "S", "Se" on the support information "li" to save are also planned. 105 means of comparing the "S" signature or "Se" listed on the support information with the computed signature are also provided and validation means 106 are used to validate the use of information stored on the coincidence of "S Signature or "Se" calculated and signature recorded on the information recording medium "li". Of course, peripheral means rated 107 input and / or display data are also provided to ensure an interactive dialogue with the user.
It will be understood that the particular device as described in Figure 8 can be used both by the holder signer information to back by the recipient of such information stored, it must then conduct an audit for signature authentication, allowing in this authentication data received.
The first and second means for storing T01 and 102 consist of inviolable storage media. It will be understood of course that the object of the invention as shown in Figure 8 the device can be constituted by a computer or a microcomputer. In case the information to back are made of a very large amount of information, such as accounting information, the computer can advantageously consist of a large computer processing power, such as an IBM PC 30/33 to operate 4,8 million instructions per second. In this case, the number of characters of the signature can advantageously be increased to 24 and a processing procedure of information in blocks marked "Bj" may advantageously be used. The programming language for the implementation of programs corresponding calculation could for example be the COBOL language. On the contrary if the number or amount of information to process, that is to say, for texts or messages of much smaller length will be considered, a microcomputer normally commercially available, may be unused. In this case, the programming language may advantageously be constituted by an assembly language. In addition, the storage devices constituting the first and second storage means 101, 102 may be constituted by inviolable storage media. In figure 8, the character of the inviolability of supports 101, 102 is represented by hatching surrounding the elements 101, 102 In the case of computers or even micro-computers, the corresponding memory areas will be provided with suitable facilities to ensure inviolability.
However, inviolable storage media may also consist of memory cards protected. This embodiment is particularly advantageous especially in the case where the device is constituted for example by a microcomputer, the microcomputer having a memory card reader protected, tending to form a new standard is currently marketing.
Of course, the embodiment of a device according to the invention by means of a microcomputer is not necessary and it may be advantageous to produce the device subject of the invention using the component or less expensive electronic system for domestic use or uses for which the amount of information or messages or texts is lower.
In the case cited above, the device enabling-implement the method of 1'invention may advantageously have to be peripheral means a display terminal of the "Minitel" type distributed by the Administration posts and Telecommunications. In Figure 9, such a device has been shown and the display terminal "Minitel" has been referenced 200 shown in this figure, the device object of the invention further comprises a memory card reader 201 protected noted, the reader having a slot 202 denoted introduction memory card 1 in the memory card reader 201 is also preferably protected with a plug 203 having read only memory cartridge which is stored in the calculation program of the signature or signatures "S", "Se". The cartridge 203 can advantageously be snap inserted into: an insertion slot 204 into the card reader 201 in the memory card reader 201 is further equipped with a microprocessor 205, the latter having the function of ensuring loading of programs stored in the cartridge 203 and loading the data stored in the memory card 1 secret data binding with the Minitel terminal 200 is provided by cable 206.
In addition, the "S" signature being subjected to encryption processing in accordance with the method as described above, an encryption program can be stored in the protected storage medium 11 of the inviolable memory card 1 zones, calculating encryption "S" signature then being made in the memory card 1 in order to ensure high system usability level vis-à-vis the user that it is the holder signatory and the recipient of such information, the device of the invention comprises a permanent memory management program "menu" type of incentive for the user, display screen interactive dialogue pages, the realization a plurality of functions, which are described in conjunction with Figure 10.
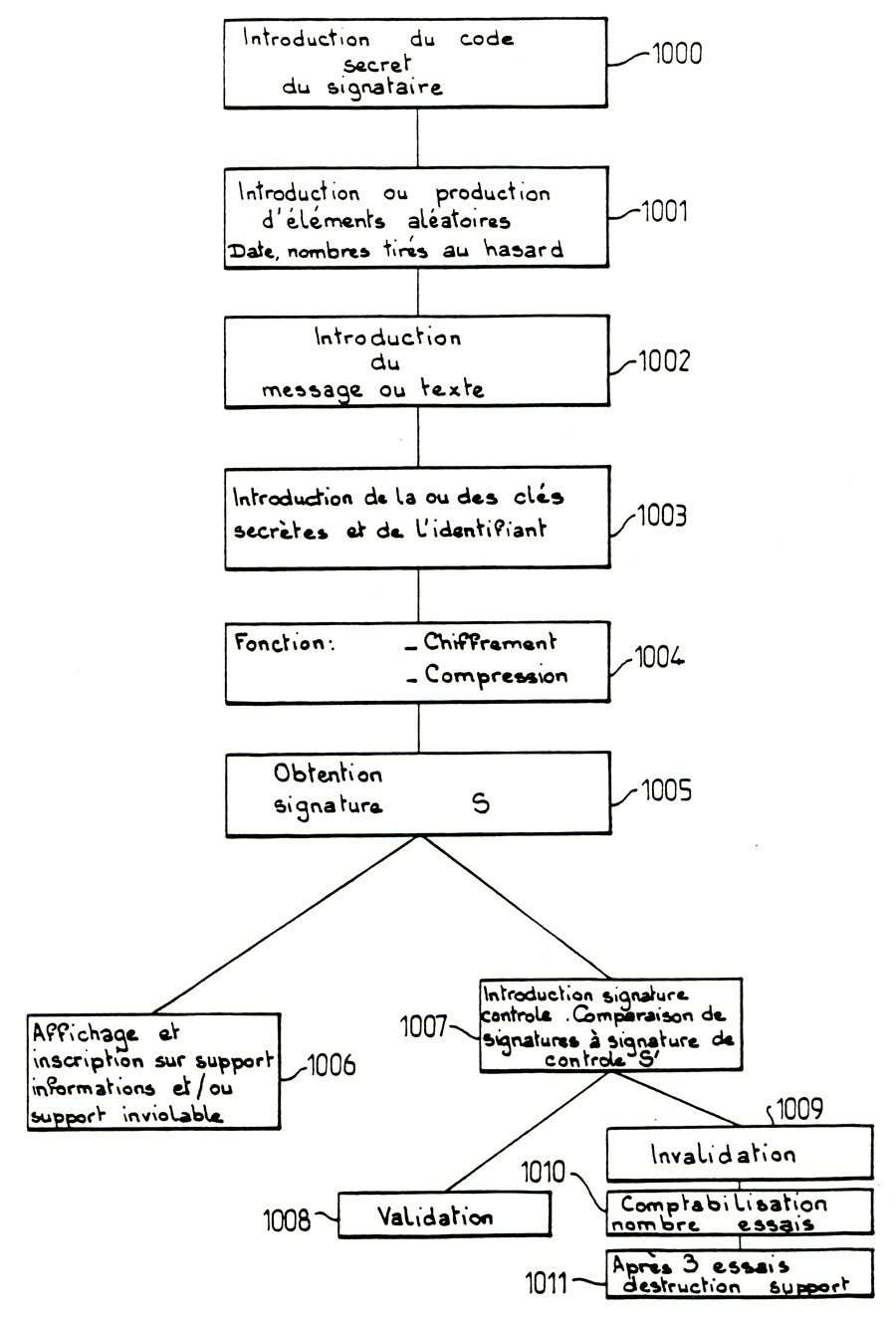
The program cited "menu" type allows first in 1000 to introduce the PIN of signatory user or recipient. Then it also allows the introduction in 1001 of arbitrary or random parameters such as date, time, or random numbers. Of course, the introduction of these parameters may be replaced by the output of these system parameters, particularly where the system in the case of including a microcomputer or a computer is provided with an internal clock from which the parameters of date and time can be directly introduced products. In addition, the "menu" program also allows the introduction of the message or text Σli to save, this operation being recorded in 1002, of course, the introduction of the secret key or keys and identifying the signatory by example is carried out in 1003 Note that in the case where a memory card is used, the introduction of the secret key or keys and the identifier of the signer 1003 is performed by means of support such as a card inviolable to protected memory, or the introduction of the secret keys stored in the protected area of the memory card one can for example be performed after inserting the card into the reader 1 201 upon introduction of the personal code of the user keyboard card reader system, the introduced or secret keys being understood themselves unknown user. In this case, the receiving user is of course holds the same memory card in which the codes and / or the parameters for calculating the signature or signatures are stored. In case, on the contrary, the device has no system memory card reader 201, it is of course always possible to introduce the secret keys and parameters for calculating the signature directly from the keyboard peripheral component of device. Of course, the degree of security required will impose the most appropriate solutions.
The program sequence for calculating modular encryption and compression, as described above in the description is then performed through the microprocessor, or the microcomputer 201 of the card reader associated with a display terminal, or, finally, by the CPU of the computer. In figure 10, the calculation of the signature is shown in stages in 1004 and 1005 After obtaining the "S" signature or any signature as defined above in the description, the display and the inscription on the supporting information and / or the inviolable support is made at step 1006 in addition, as shown in Figure 10, the management program type menu also allows a user to input the recipient's signature to be verified for comparison with the stored or transmitted signature. A comparison of the recorded information on the support of "li" and the test signature "S" signature S is then performed, the aforementioned operations in 1007 being shown in figure 10 In case of coincidence of the test signature S 'and' S 'signature, then the device performs a signature validation and information transmitted in 1008.
As shown also in figure 10, where an invalidation signature is obtained in step 1009, the LCD screens have a screen page signaling the risk of destroying the memory areas of the inviolable support after a specified number of unsuccessful attempts signature validation. Screen displays are shown above for example in 1011, after a stage of counting the number of unsuccessful attempts in 1010 represented of course be understood that the procedures for signing and signature validation set-in-œuvre by the device described above are separated. The validation process is conditionally authorized signature for identifying user identification codes, so the recipient user, separate identification of the signatory user codes. Thus, this procedure allows the recipient to verify user ID signature that he can not write himself. The only knowledge required to identify recipient user for this operation is for example the PIN, for example consisting of alphanumeric characters of information or signatory holder.
Another particularly interesting application of the method and device of the invention will now be described also with reference to Figure 10 In accordance with a particular aspect of the apparatus and method of the invention, for a random number determined identification introduced in 1001 by the user, which has the code of this random identification number, the introduction of a pseudo-information back in 1002, pseudo-information consisting of an identical repetition of characters "li" determined on an arbitrary number of characters used to generate a random representative inviolable temporary access code for that user. On transmission identification code and random identification number to a receiving user, the validation procedure of temporary inviolable random access code is allowed. It will be understood of course that the pseudo-information may consist of any arbitrary nature, such as an alphanumeric character ASCII and extended in a particular spacing, the latter being capable of providing the minimum probability of error for the introductory phase of a message or text on the pseudo-information.
It will be understood that the representative random inviolable temporary user access code is of course in the calculated pseudo-information sign which was added by concatenation, the random identification number entered by the user. The method used is thus particularly advantageous in that it allows for a course organization server, such as a database, the identification of any subscriber, from temporary random codes representative of that subscriber. Thus, access to the server or the corresponding database is protected by a system of completely renewable access code for which the renewal period may be taken arbitrarily at the initiative of the server organization. Indeed it is understood that the change in the character repeated identically on the initiative of the member server allows actually cause a complete change of pseudo-text or pseudo-information necessary to generate the identification code or access. The method and the device of the invention and are particularly advantageous in that they allow, on the one hand the protection of the access to the server and also qualitative Organization backups of modifiable or erasable carrier scanned data this server where data is online, by establishment of a reference library organization.
Applications of the method and device object of the invention is however not limited to this use only.
Thus, the method and the device of the invention can advantageously be used for data exchange with the outside, the recipient of the information, keeping the seals already checked, easily avoiding double reading. Furthermore, in the case of remote network devices, the signature can be used to protect files locally entered. It is indeed easy to verify that the signer is authorized in payroll, billing or similar to the central computer and the data has not been altered. The signature may also be used to ensure the prevention against the double reading, in this case, only the signature is compared with the previously calculated signatures. In case of coincidence of signature, it indicates the existence of a playback of the corresponding file. The method and the device of the invention may also be advantageously used for the management of distributed programs. Indeed, in a network containing programmable local terminals, central computer must be able to ensure that all terminals have current copies of the correct programs. Such verification can be done by sending periodic a key, from the host computer to each terminal. Each of these then calculates a new seal or signature from the program text and the new key. Transmission on each end of the new signature to the host computer, it compares the seal for each of the terminals, from the text of the SMP. The identity of the signatures or seals, the programs will be considered identical.
In addition, the method and the device of the invention are used to ensure the absence of errors in the software distributed to a large clientele. To this end, the provider distributing the software can compare the seal of the software package was originally placed with clients with that of the actual program, to prove the existence or non-existence of errors or omissions.
The method and the device of the invention can also be advantageously used to verify that no changes have been made to files between regular use of these files. Similarly, checking control totals, accounting or financial statements can be made. In this case, the use of the method and device object of the invention can guarantee that there is no deliberate manipulation or inadvertent errors even in the above statements. Another particularly interesting application of the method and device object of the invention consists in the storage of information, such as accounting information. Indeed, some national laws require that the accounting information is archived for a specified period, usually ten years. Of course, these national laws also require fully satisfactory with respect to the safety of maintaining the integrity of the information conditions. Magnetic storage is permitted, the method and device of the invention may advantageously be used to verify that the information is intact and unchanged, even after many years of storage.
In addition, the method and the device of the invention can advantageously be used to give each backup information databases, to assign to them a truly representative seal or signature content these copies. So when you need to use the copies provided with their seal or signature to restore information from a corrupted database, the signature can be verified before reloading.
Finally, the method and the device of the invention can be used to verify the identity of a given date files used by subsidiaries of the same company locally and centrally. In this case, the calculation and comparison of only seals or signatures allow for the file to ensure and guarantee the identity of this file.
Of course, the method and the device of the invention are not limited to qualitative backup of digital information. They can advantageously be used for the generation or creation of encrypted keys inviolable from a public key. In this case, you only course that the sender and the receiver of the encrypted key to be able to-implement the method of the invention from secret parameters on the same public key, the transmission of this latter can be freely accessible to the public and secret parameters are being transmitted securely or stored on a tamper resistant bracket, gender memory card and sent to the issuer and recipients for the same treatment.
We have thus described a method and device quality of digital information stored on a backup medium erased or modified, high performance. The high performance of the method and device object of the invention relate to the cryptographic strength of the signature produced in accordance with the method of the present invention. The cryptographic strength appears to result from the fact that a given text may generate essentially any signature or seal. Under these conditions, only an exhaustive search would compute the secret key from a text and its seal or signature. The method and the device of the invention are also remarkable in that a particular text can generate any signature, this property appearing as an additional guarantee cryptographic strength. In addition, the signature algorithm is a non-switching function data. If you change any subset of the data, it was he reduced to a number, the signature will be totally different. The method and the device of the invention may in particular be-implement in the case of the transmission of accounting data such as for example the data relating to the clearing bank. Choosing a size of signature, that is to say, a sufficient number of characters, virtually excludes an exhaustive search of the secret keys.
SMART CARD APPLICATIONS IN SECURITY AND DATA PROTECTION,
By Jean GOUTAY, President of the INFOSCRIPT society.
INTRODUCTIONThe several security elements of the smart card are based on physical and logical barriers.
- Materially, the smart card is a monolithic component including a microprocessor and a memory of 8 kbits, this memory being indelible.
- In addition entry test points have been destroyed before activating the smart card.
- In practice it is impossible to read, modify or duplicate the contents of the smart card.
- Logically, the chip is able to memorize the different wrong access attempts and invalidate the electronic circuit after three repeated attempts for example or "N" attempts on the whole.
- Let’s see in addition that the dialogues between the chip and the exterior depend on a random value, which is a known element of security and a protection against the passive intrusion and possibilities of simulation.
- What are the uses of the smart card, specially in matter of protection of information and more generally in security ?
- They concerned:
- identification,
- authentication,
- enciphering and key management.
- They allow the security of:
- the access to premises or to a network,
- the payment at P.O.S. or at distance,
- the transmission in networks, electronic messeging for instance,
- access to services such as: broadcast videotex or toll TV, interactive videotex, database.
First let’s look at the different uses of the smart card.
- Portable Protected Data
- The smart card contains a memory not very big (from eight to sixteen K) but protected against the exterior by a microprocessor (or a firmware) and it is possible to store in it clear confidential data. These data will be accessible only on production of a secret code. The application are : protected portative file such as medicine, student portable file,…
- However the smart card is able probably to encipher short messages, store and transmit them. In particular this system can be used for sending enciphered keys at distance.
- Identification
- the finger prints,
- the speech,
- or the dynamic signature.
- Software protection
- Data Authentication
- or at the level of running with computation elements in the program required the presence of the smart card,
- or with holes in the program which can be restored with the smart card only.
- Reciprocal recognition and access control
- Card authentication by general system
- the authenticity of the smart card and of the bearer,
- the guarantee limit,
- possibility the black list.
- Exchange of enciphered data
- The telepayment
- the bank statement display,
- the remote cash transfer,
- the telepayment of goods providers as retraiters "La Redoute".
- the sure identification of the suscriber,
- the encipherment of messages on line and generation of "certificates" ensuring it’s integrity and giving the proof that the information is well registered in the card.
- Protected electronic messaging
- Broadcast interactive videotex
- one using the preliminary enciphering and decoding informations thanks to the smart card for those who have paid?
- the other one (pre-payment) permitting the access to the services after having destroyed bits area in the card, previously credited.
Thanks to the content of the secret and inviolable area in the smart card, thanks to computation which remains with in the card, it is possible to verify a personal code with a very good security and so to identify the card’s bearer.
But a better identification can be obtained by a more secure storage of patterns bounded with physical characteristics of the person, such as:
After data compression by an algorithm (hash code,…), it is possible to compute and to store in the smart card an "electronic signature", function of this compression and of the transmitter identity. In another connection this signature is added to the original text, a fact wich permits the verification.
This process can apply for the certification of accountant, original documents, banking orders and transfers, files and software, at different levels of development for instance.
In matter of software protection, several systems can be envisaged, wether at the transport level with the encipherment of the software and the deciphering key stored in the smart card,
It is easy to see the applications in the domestic computers area or in the area of video cassettes.
We can see in this case that decoding must be put at the monitor level.
Now let’s see other applications.
A simple algorithm computed in the card permits verification, with a random value "E", that the two cards are well matched, e.g. Ra=Rb.
Wether in the case of the access control to premises, or a network or a data base.
In the network case, every passive intrusion on the line does not allow either listening or simulation or re-use of the dialogue, the informations being completely random.
In the case of access control, the combination changes at every access because the key "R" is fugitive.
Another application can be the recognition of the smart card by the system, that is to say it’s authenticity, based in theory on public key use.
Using a random message "M", the system computes C=f (M), "f" being the public key. "C" is transmitted to the card which contains the secret part of the function.
The big advantage is that the system, which can be a general public terminal, doesn’t require any secret function.
So in the case of electronic payment at point of sale, the system verifies:
Let’s see in this case that the card allows the management of several access codes : banker code for the valorization, bearer’s code, service providers codes…
But the possibilities of the smart card are even more interesting in the networks, in matter of security.
In addition to the previously described functions, they allow the automatic logging the management of preloaded credit fields and if they can’t encipher at this moment they provide solutions to the delicate problems of key management.
With a generator of enciphered bits an a random number "E", messages can be enciphered thanks to the smart card along a network, with keys "R" which can be changed at a desire frequency.
In particular the enciphering algorithm "A" can be very simple.
This system can be set up on any encipherment equipment in networks and provides a solution to delicate problems of key transportation.
One application is given in electronic mail where the cards are used for reciprocal identification of interlocutors and encipherment of informations by fugitives keys.
Let’s see now very present applications.
The first wordwide experiment of telepayment has been in Velisy, near Paris, "TELETEL" and allows a suscriber to make from a videotex terminal, the minitel:
The smart card (with it’s reader) consequently permits:
All is in an environment at distance non controlled.
The security of the system is based on the exchange of fugitive random keys.
Another system of telepayment would be possible.
With the use of public keys and the signature of the messages by a secret key of the user, whose the public part, signed by the key of the bank, would be transmitted previously by the user. This system doesn’t require any black box at the central processor.
General systems can be envisaged to protect in addition informations during the storage in the mailbox of the service computer.
It is possible for example to encipher on line the data, and to decipher them immediately with synchronous mode, finally to encipher again with another key for the storage.
It would be possible also the envisage another scheme with the use of public key for authentication of the transmitter, but also for transportation of the random key the message being enciphered it self with this key changing at every message.
In the case of access to toll services, whether broadcasted programs or videotex services or data base, we have two possible systems :
In conclusion, by its vast possibilities not yet explored, the smart card open new vistas in matter of security, networks and data protection.
Thank you for your attention.

PCT Patent / Smart card applications
